A new digital border wall for your network, datacenter or device? Compromise of the wrong database can be catastrophic to a nation, customers, the organization – and you!
United States “data sovereignty” can be better protected
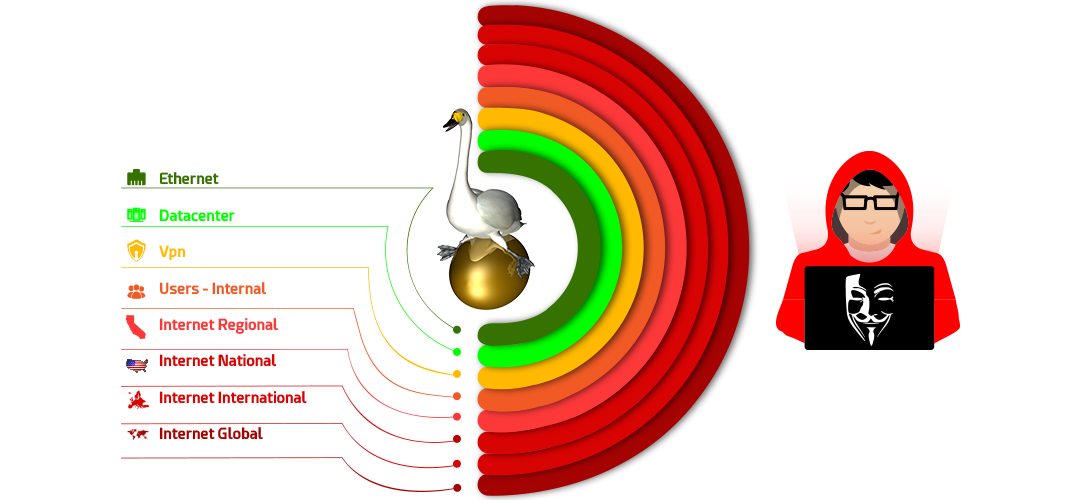
United States “data sovereignty” can be better protected, shielding high value data from foreign states, and internal user threats alike. Hop Sphere Radius security algorithms create a perimeter by limiting the number of hops network packets traverse as they go through routers. As each packet passes, routers decrement a toll (hop count value) until hop count is exhausted and the packet discarded. Packets are discarded by design to prevent packets looping infinitely. All TCP/IP device default settings have enough tollto circle the world multiple times, opening compromise to hackers outside the required communications sphere.
Don’t firewalls protect from such situations?
Don’t firewalls protect from such situations? Ask any compromised organization having spent huge budgets on every security firewall appliance known to man – not always. A digital border can be set on each device uniquely to its appropriate sphere. Safety can be magnified beyond firewalls by setting a digital border on the device itself, without dependence on a secondary device, providing additional individual security.
Wouldn’t it be comforting to know the server containing critical data or the biomedical device maintaining a loved one in the hospital had an individual digital border so it cannot directly communicate to a hacker?
Wouldn’t it be comforting to know the biomedical device maintaining you or a loved one in the hospital had an individual digital border so it cannot directly communicate beyond the hospital to a hacker, even if firewalls were misconfigured or failed? Every compromised organization had many firewalls, yet they were vulnerable. And if that isn’t enough, NSA’s own hacker toolkit, recently compromised, gave hackers new automated “point and shoot” tools to break into firewalls and servers. We desperately need powerful individual digital borders providing an additional layer of security.
Can your most valued database open a direct tollway to China or Russia right now?
Can your organization’s most valued database open a direct tollway to China or Russia right now? Many can, because they allow software updates via the Internet – huge fail. Complaints about foreign state and hacking from beyond the United States are prevalent. Why are high stakes, high value devices allowed to have the ability to connect to distant hackers simply for the convenience of direct internet updates? Eighty percent of nuisance and real hackers are located outside the United States beyond the rule of law. Thousands of unsophisticated nuisance hackers and terrorists running “script kiddie” Internet downloadable hacker tools are consuming massive firewall processing and human resources, of which, 80% can be eliminated by changing Hop Sphere settings.
What we’re doing is not enough … we are by our own reports losing the cyber battle.
At the recent RSA Conference in San Francisco much discussion was about the “Reasons Why We’re Losing The Cyber Battle”. Awaiting my turn to present at a military Cyber-Symposium, I listened as cyber commanders bemoan how international state sponsored hackers are compromising their highly secured systems. Digital borders stop foreign hackers ability to directly connect to U.S. systems. Rhetorically, do we need foreign governments accessing our military servers?
high stakes experience … escorted by heavily armed forces into the Pentagon following 911…
I was reminded of being escorted by heavily armed forces into the Pentagon immediately following the 911 disaster for communications recovery. Our military hit at its heart, shocked, yet resolute to overcome. One can only imagine what it must have felt like to experience such a blow as a commander. And now it’s a new war – digital cyber warfare.
I was challenged to find a solution – remembering years of deep packet security analysis starting in the early eighties “staring” at protocol analyzers at Lockheed in Sunnyvale and later working with Harry Saal and Len Shustek inventors of “The Sniffer” at the Network General startup (now NetScout). I considered having trained 50,000 professionals in Network Forensics having certified over 3,000 as Certified NetAnalysts across 27 countries, and later serving as Technology Officer at NetQoS/CA Technologies solving complex problems on the world stage.
I’ve been challenged by thousands of network forensic professionals that are 98% hyper critical technical thinkers. In training they play “stump the chump”, an affectionate term for challenging an instructor’s knowledge. Liken it to President Donald J. Trump’s unabashed challenge to his opposition. Let’s just say I’ve been “schooled” in network application and deep packet security theory and it continues with the emergence of Hop Sphere Radius Security.
Grasp the TCP/IP theory… be open to this “not-so-new” solution
Consider this “not-so-new” idea, grasp TCP/IP hop theory, without dismissing its ability to be rapidly deployed and unique device security benefits. After careful consideration, most wonder why we didn’t change default Hop Sphere long ago – broadly.
Saal remarked “this is a nice and clean approach to reducing the exposure surface, and well worth implementing broadly…”
Network General founder Harry Saal remarked “this is a nice and clean approach to reducing the exposure surface, and well worth implementing broadly, not only in governmental circles”
Safety can be magnified by setting a digital border on each device, network or data center individually, denying hacker direct connection despite firewall misconfiguration or failure
Learn more about adding powerful new digital borders to prevent:
- Database and Data Center Compromise – Keep packets inside data center even when firewalls fail.
- Foreign State Hacking – stop Russia, China and others from direct access, preventing lateral positions.
- Internal User Threats – limit general user access to high value databases.
- IoT Device Takeovers – protect cameras and IoT from faraway hackers.
- DNS Web Redirection – to Foreign Locations “Beyond the Rule of Law”
- Nuisance Deep Web “script kiddie attacks” – from consuming security device and human resources.
Click here to receive more information on Hop Sphere Radius Security Algorithms.